The operation Black Basta Ransomware has created an automatic charge for the period of rudeness, which gained underneath the title “Bread” to violate the EDGE community units, corresponding to firewalls and VPN.
The construction allowed BlackBasta to optimize the preliminary assaults of get admission to to the community and scale extortions to susceptible ultimate issues which have been uncovered to the Web.
Brude detection comes from the ECLECTICIQ Arda Büyukkaya researcher after an in -depth learn about of the leaked inner magazines of the Ransomware Bang gang.
A number of stories of huge -scale assaults and spraying passwords on those units all over 2024 all over 2024, a few of that may be related to the operations of the inflater or an identical beginning.
Automation of tough -ups
Buyukkaya says that Black Basta has been the use of the Brudeed computerized platform since 2023 to habits massive -scale assaults and impolite assaults in community units for community units.
The research of the supply code signifies that the construction was once specifically designed for accounting information at the following VPN and far flung get admission to: Sonicwall Netextender, Palo Alto Globalprotect, Cisco AnyConnect, Fortinet SSL VPN, CITRIX NETSCALER (Citrix Gateway), Microsoft RDWEB (Retepetop Destop and Watcherarey), Watcerars-Watepn), Watchrare), Watcerars-Watepn, Watepn.
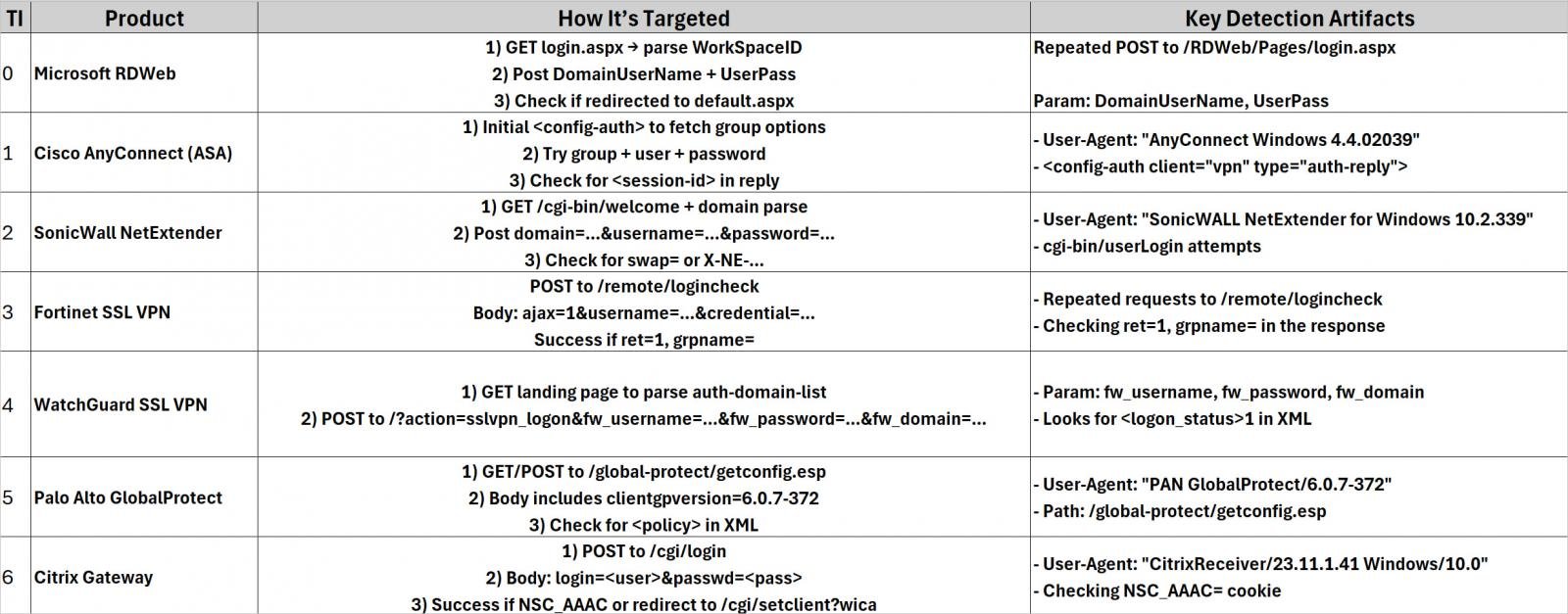 The assault method used for every product
The assault method used for every product
Supply: ECLECTICIQ
The framework is searching for publicly to be had community units alongside the perimeters, similar to the checklist of goals by way of list subdomains, resolving IP addresses and including prefixes corresponding to ‘.VPN’ or “remote”. Fits are communicated at the server of command and regulate (C2).
Once doable targets are recognized, Brude extracts a password from a far flung server and combines them with in the neighborhood generated assumptions to satisfy many authentication requests the use of a number of CPU processes.
Buyukkaya shared the supply code the use of BleepingComputer, which presentations how the device makes use of particular requests and person brokers for every goal software in gross assaults.
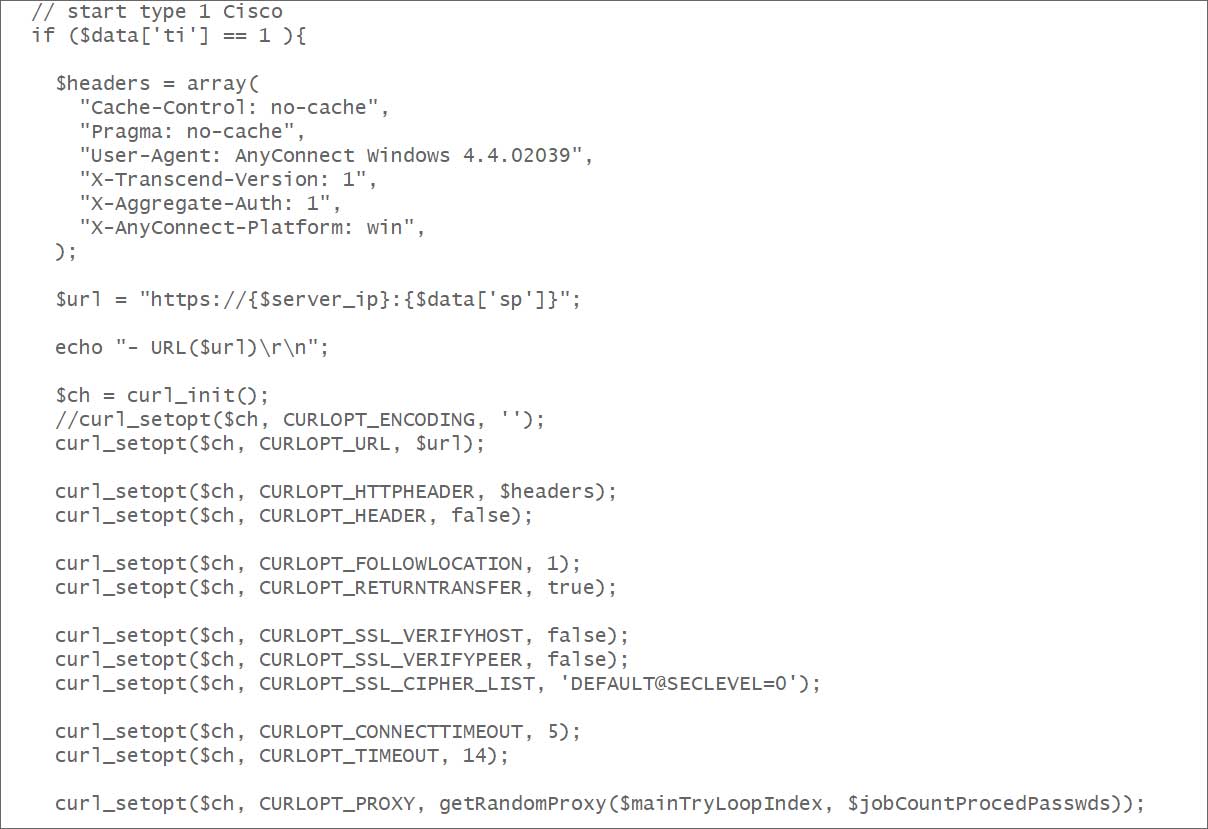 The supply code for the impolite drive of Cisco AnyConnect (ASA)
The supply code for the impolite drive of Cisco AnyConnect (ASA)
Supply: BleepingComputer
The ECLECTICIQ document says that Brude can extract the overall title (CN) and selection gadgets of gadgets (SAN) from SSL certificate of goal units, which is helping generate further guesses of passwords primarily based on track domain names and naming.
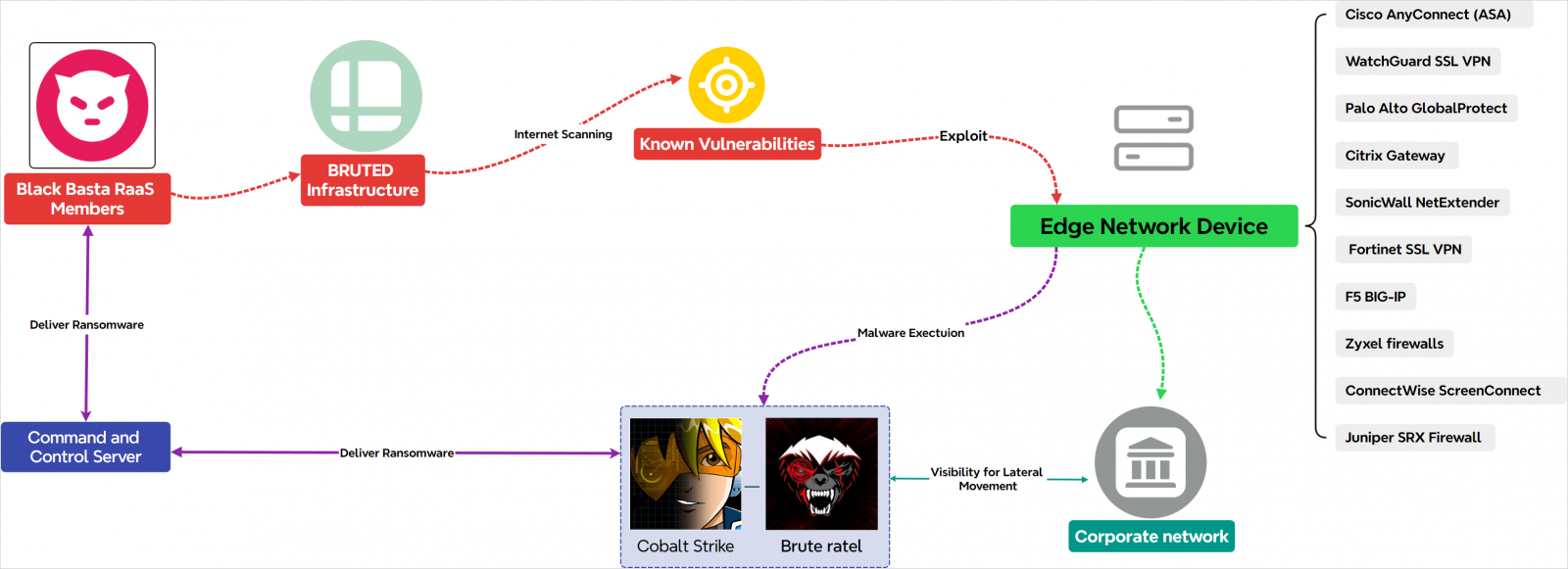 Overview of Black Basta assaults with the participation of Bruded
Overview of Black Basta assaults with the participation of Bruded
Supply: ECLECTICIQ
To keep away from detection, an inventory of proxy -proxy servers SOCKS5 with an enchanting area title is used throughout the framework, which hides the infrastructure of the attacker outdoor the intermediate layer.
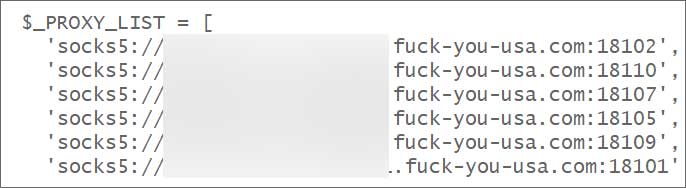 Proxy servers utilized by Black Basta’s Busted Framework
Proxy servers utilized by Black Basta’s Busted Framework
Supply: BleepingCopouter
Its major infrastructure contains a number of servers in Russia and is registered in keeping with Proton66 (like 198953).
Chat magazines additionally published inner discussions in regards to the server downtime because of unpaid charges that had been due to this fact up to date, which gave us an concept of the day by day operations that experience to handle.
Gross -howl coverage
Gear corresponding to BriedLine Stranline Ransomware, by way of violating many networks concurrently with minimum efforts, expanding monetization alternatives for risk contributors.
The important thing coverage is to make sure compliance with robust, distinctive passwords for all EDGE units and VPN accounts and the usage of multifactorial authentication (MFA) to dam get admission to, despite the fact that the accounting information is compromised.
Additionally it is necessary to regulate authentication makes an attempt from unknown places and malfunctions in a top quantity and introduce restriction of the rate and coverage of blocking off accounts.
Electiciq shared the checklist of IPS and domain names utilized by Bruded, which can be utilized to create new firewall regulations that block requests from a smartly -known malicious infrastructure.
Whilst Brude does now not use any vulnerabilities for violating Edge Community units, it’s nonetheless necessary to enhance those units in an up to date state, the use of the most recent safety updates.

In keeping with the research of 14 -meter malicious movements, to find the ten perfect strategies of Miter Att & CK, status for 93% of assaults and the way to give protection to your self from them.
Learn Purple Document 2025



