The hot social engineering marketing campaign was once aimed toward candidates within the Web3 area with pretend interviews the use of a malicious software for “grassy” conferences, which establishes malicious instrument for the robbery of cryptocurrency wallets.
Fraud affected masses of folks, a few of them reported that their wallets have been exhausted in assaults.
The telegram staff was once created to speak about the assault and for individuals who are affected to assist each and every different take away malware infections from Mac and Home windows gadgets.
Social engineering assault Grasscall
The marketing campaign was once held by means of a Russian -language “trade team of trade”, referred to as Loopy Evil. This staff conducts social engineering assaults to power customers to load malicious instrument on their Home windows and Mac gadgets.
This staff of cybercrime is understood that it’s aimed toward customers within the cryptocurrency area, the place they advertise pretend video games or employment alternatives on social networks.
Customers are deceived within the instrument set up that deploys malicious instrument to do away with data on gadgets that can be utilized to scouse borrow passwords, cookies and wallets from compromise compromises.
With the conversion with the Choy, a qualified Web3, who was once aimed on the assault of social engineering, BleepingComputer reported that the actors of the risk created a fancy persona on-line, consisting of a site and social networks on X and Linkedin, the place they pretended to be an organization named Weachseker.io.
Then the actors of the threats started to acquire bonus lists of vacancies on LinkedIn, Wellfound and Cryptojobslist, one of the vital standard web sites for WEB3 and BLOCKHAIN.
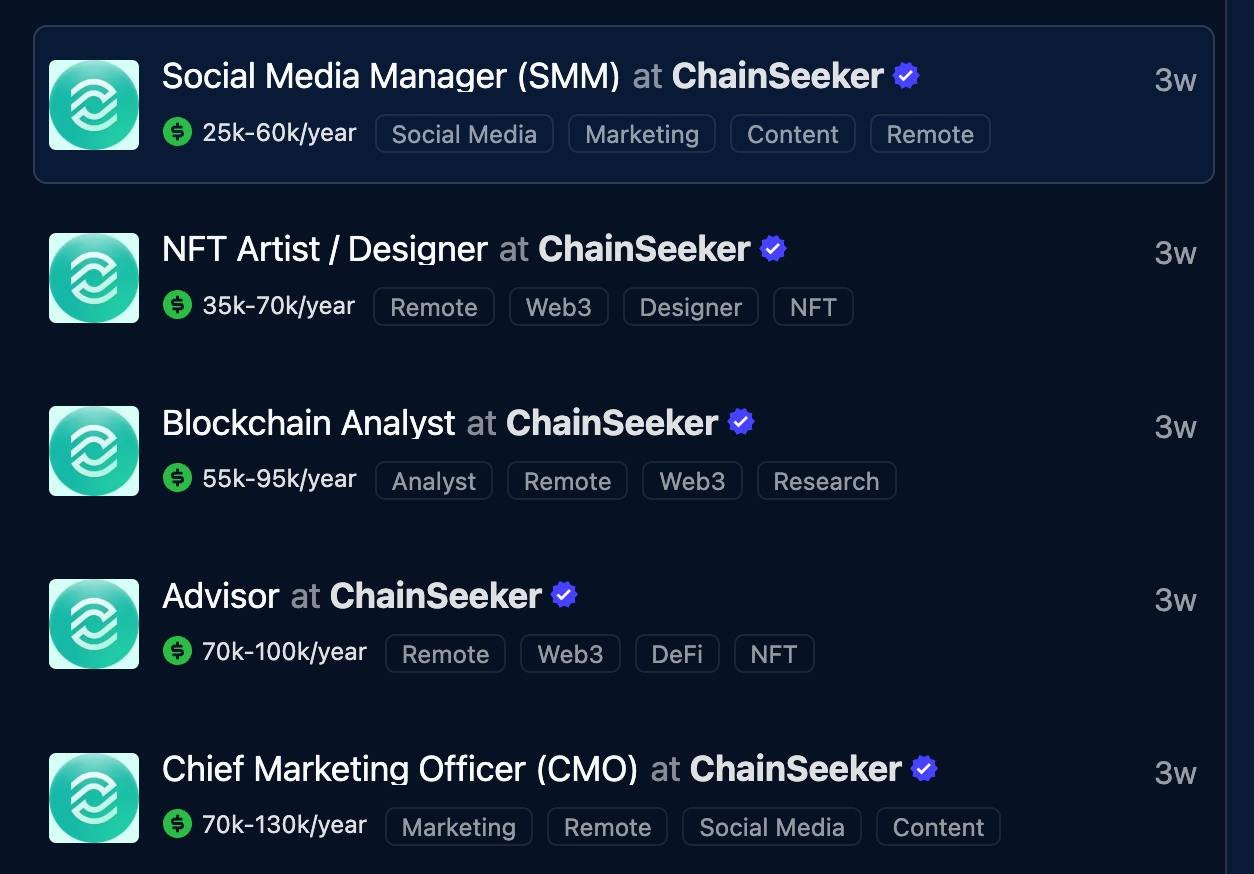 The duty of chains promoted on Cryptojobslist
The duty of chains promoted on Cryptojobslist
Supply: Choi
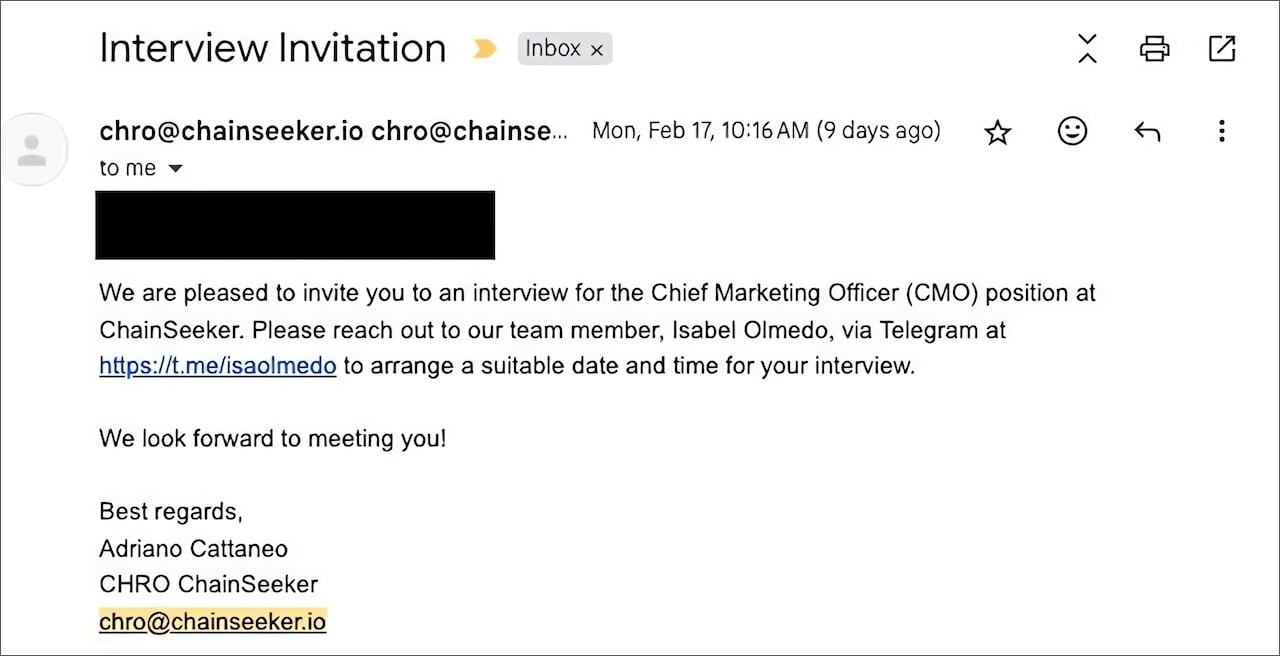 Invitation to an interview from Faux Cheatseeker Corporate
Invitation to an interview from Faux Cheatseeker Corporate
Supply: Choi
When contacting touch, the pretend director of CMO will tell the targets what they wish to obtain instrument for video conferences referred to as “Grasscall” the use of the internet website and code incorporated.
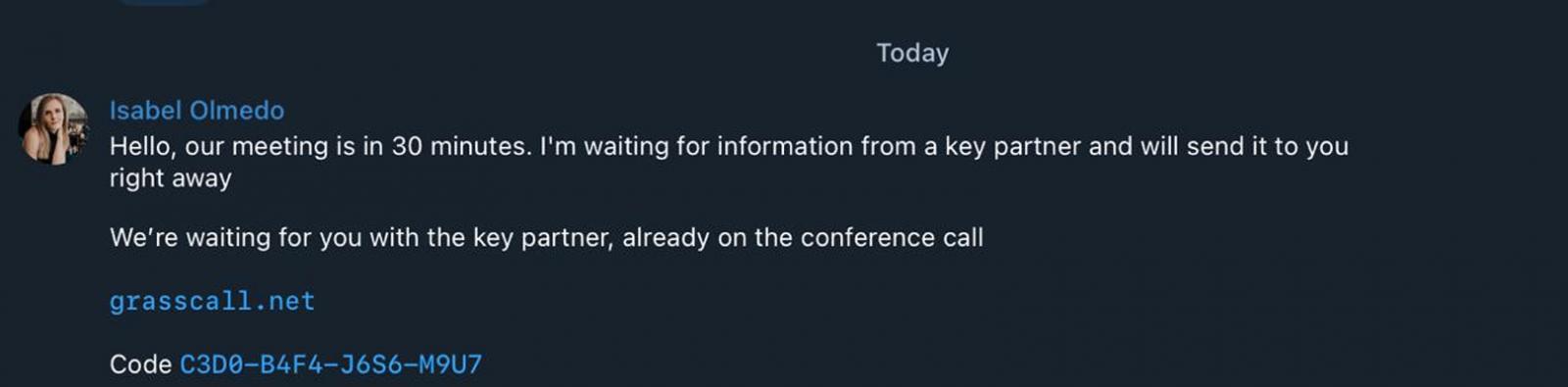 Telegram dialog with the executive advertising director of Faux Cheanseeker
Telegram dialog with the executive advertising director of Faux Cheanseeker
Supply: Choi
GRASSCALL instrument was once downloaded from GRASSCALL (.) NET, and both the Home windows shopper or the MAC will be offering, relying at the consumer agent of the customer browser.
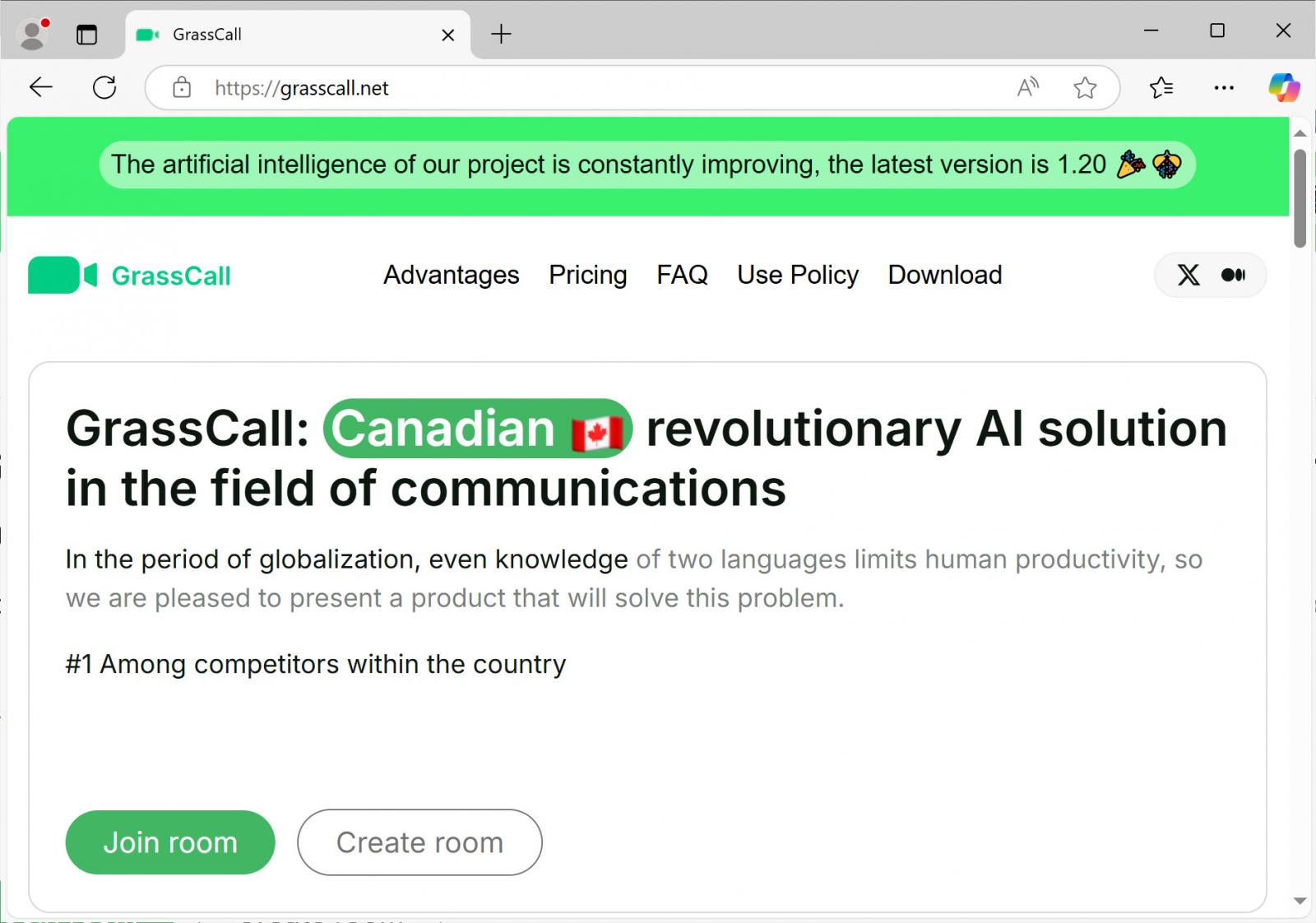 GRASSCALL (.) Internet internet website
GRASSCALL (.) Internet internet website
Supply: BleepingComputer
The Cybersecurity researcher G0NJXA, who displays those actors -UGROS, mentioned BleepingComputer that the Grasscall site is the clone of the Gatherum site used within the earlier marketing campaign. The researcher says that those web sites are used as a part of the assaults of social engineering carried out by means of the loopy evil subgroup, referred to as “Kevland”, which could also be described within the “Future” file.
“The necessities assigned to assemble are supplied by means of the fraud control handbook. Gatherum is managed by means of Loopy Evil Subteam Kevland, which internally tracks the InSikt Crew as CE-6. “
When guests are seeking to obtain the Grasscall software, they’re going to be invited to go into the code, the average CMO pretend director in Telegram.
By way of getting into the proper code, the site will both be offering the buyer “Grasscall.exe” (Virustotal), or the MAC “Grasscall_v.6.10.dmg” (Virustotal). When imposing, each methods will determine malicious methods for the advance of data or trojans of faraway get right of entry to (rat).
On Home windows gadgets, the FAKE Assembly software will set up the rat with the infosteiler, akin to RHADAMANTHYS. On MacS, he’ll set up an atomic (AMO) computer virus.
“The rat is used to create resistance in the car, add also for the password and deploy a fingering seed for solid wallets,” defined G0NJXA.
When acting, the malware will attempt to scouse borrow recordsdata according to key phrases, cryptocurrency wallets, passwords saved in the important thing fit of Apple, in addition to passwords and authentication recordsdata saved in internet browsers.
The G0NJXA instructed BleepingComputer that the stolen data is loaded at the servers of the operation, and the details about what was once stolen is printed within the telegram channels utilized by cybercrimination.
“If the wallet is found, the passwords are loaded and drained assets, and the user is paid a payment that forced the victim to download fake software,” mentioned BleepingComputer researcher.
The researcher says that the details about bills for individuals of Loopy Evil is publicly posted in Telegram, appearing that individuals of this operation can do dozens, if now not masses, out of hundreds of bucks for each and every sufferer that they effectively dissipate.
 Loopy evil cost printed in Telegram
Loopy evil cost printed in Telegram
Supply: G0NJXA
In accordance with the assaults, Cryptojobslist deleted the vacancies lists and warned those that said that they have been fraud and scanned their gadgets for malicious instrument.
From the general public consideration to this rip-off, the topics of the risk, by means of the visual, stopped this particular marketing campaign, and the site is now not to be had.
However, for individuals who mistakenly put in instrument, it is crucial to modify passwords, passafras and authentication tokens for each and every site that you simply seek advice from, and cryptocurrency wallets that you simply personal.
Additionally it is necessary to incorporate two -factor authentication on all websites that toughen it the use of the authentication software. After turning on, although your accounting knowledge is stolen, risk actors won’t be able to get right of entry to your account with out your 2FA codes.
The G0NJXA says that the actors of the threats moved to a brand new marketing campaign referred to as Vibecall, the place risk actors proceed to make use of the similar website template as Grasscall.
Even supposing he isn’t hooked up with Loopy Evil, a cybersecurity researcher Malwarehunterteam, who additionally tracked those campaigns, warned BleepingComputer concerning the new marketing campaign of malicious methods, pretending to be the sport NFT Blockchain underneath the title Mystix.
Like different campaigns of those actors, the sport is aimed toward video games within the crypto -space and makes use of an identical malware to scouse borrow handbag for cryptocurrency.



