The not too long ago came upon garage operation, the alternate buffer, referred to as “Massjacker”, makes use of a minimum of 778 531 addresses of cryptocurrency pockets to scouse borrow virtual belongings from compromise compromise.
In line with Cyberk, which came upon the Massjacker marketing campaign, about 423 wallets related to the operation contained $ 95,300 on the time of research, however ancient information recommend extra important transactions.
As well as, there’s one soly-wallet, which the actors of threats, it sounds as if, are used as a central middle for receiving cash, which has nonetheless raised greater than $ 300,000.
Cyberark suspects that all the Massjacker operation is related to a selected workforce of threats, because the report names downloaded from command and keep an eye on servers and encryption keys used to decrypt recordsdata have been the similar all over the marketing campaign.
However, the operation can nonetheless be adopted by way of malware fashions as a provider the place the central administrator sells get entry to to quite a lot of cybercriminals.
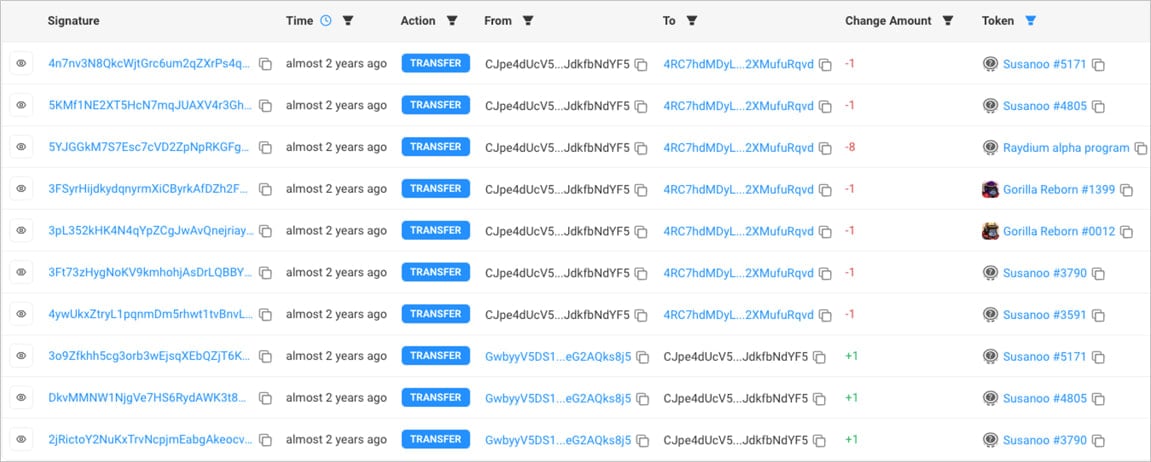 Transactions at the Solan pockets
Transactions at the Solan pockets
Supply: Kiberark
Cyberark calls Massjacker a cryptoca operation, even if this time period is extra regularly related to unauthorized cryptocurrency mining the usage of the processing/{hardware} assets of the sufferer.
In truth, the Massjacker is depended on on interception within the buffer of the huge fence (Clippers), which is a trojan horse that controls the Home windows alternate buffer for copied addresses of the cryptocurrency pockets and replaces them with one beneath the keep an eye on of the attacker.
Thus, the sufferers unconsciously ship cash to the attackers, even if they sought after to ship them to any individual else.
Clippers are easy, however very efficient gear which are particularly tricky to discover from their restricted capability and operational quantity.
Technical main points
Massjacker spreads via Pesktop (.) COM, a web site that puts pirate device and malicious device.
Tool installers loaded from this web site carry out the CMD script that launches the PowerShell script, which receives the Amadey bot and two loader recordsdata (Packer and PackerD1).
Amadi launches Packere, which, in flip, deciphers and a lot PackerD1 into reminiscence.
PackerD1 has 5 constructed -in assets that build up its evasion and anti -analysis productiveness, together with connecting to that point (JIT), show metadata tokens to intimidate practical calls, in addition to a person digital gadget to interpret instructions as an alternative of normal .NET code.
PackerD1 deciphens and introduces PackerD2, which in the end decompresses and gets rid of the general helpful load, Massjacker and introduces it into the felony technique of Home windows ‘Stalutil.exe.’
.jpg) Masket chain of an infection
Masket chain of an infection
Supply: Kiberark
Massjacker controls the alternate buffer for the cope with of the cryptocurrency pockets the usage of REGEX drawings, and if the twist of fate is located, it replaces it to the pockets addressed by way of an attacker from the encrypted record.
Cyberark calls at the analysis neighborhood of cybersecurity to appear after huge cryptocching operations equivalent to Massjacker, as a result of, regardless of the perceived low monetary harm, they are able to reveal treasured details about the identity of many risk members.

In keeping with the evaluation of 14 -meter malicious movements, to find the ten absolute best strategies of Miter Att & CK, status for 93% of assaults and the way to give protection to your self from them.
Learn Purple Record 2025



