A brand new find out about published additional connections between Black Basta and Cactus and Gransomware gangs, and members in each teams use the similar assaults of social engineering and proxy-volunteer techniques of BackConnect for get admission to after operation to company networks.
In January, Zscaler came upon a malicious instrument pattern in Zulater, which contained what appeared a brand new DNS tunneling serve as. Additional research of Walmart confirmed that Zulker dropped a brand new proxy instrument, which is named BackConnect, which contained hyperlinks to a malicious code for QBOT (QAKBOT).
Backconnect is a malicious instrument that acts as a proxy software for far flung get admission to to compromised servers. Backconnect lets in cybercriminals to spend a tunnel, confuse their actions and escalate assaults within the surroundings with out detection.
It’s believed that each Zloader and Backconnect are associated with the black operation of BASTA extortionists, and members use malicious instrument for violation and allotted via company networks.
Those connections are moreover bolstered via the new BlackBasta knowledge leak, which published inner conversations of the operation, together with between the executive of the extortion gang and somebody, who is thought of as the QBOT developer.
Hyperlinks
Black Basta is a gang of extortionists, which used to be introduced in April 2022. It’s believed that it comprises individuals of the group of air conditioners, which closed in Would possibly 2022 after she suffered an enormous leakage of the supply code and inner conversations.
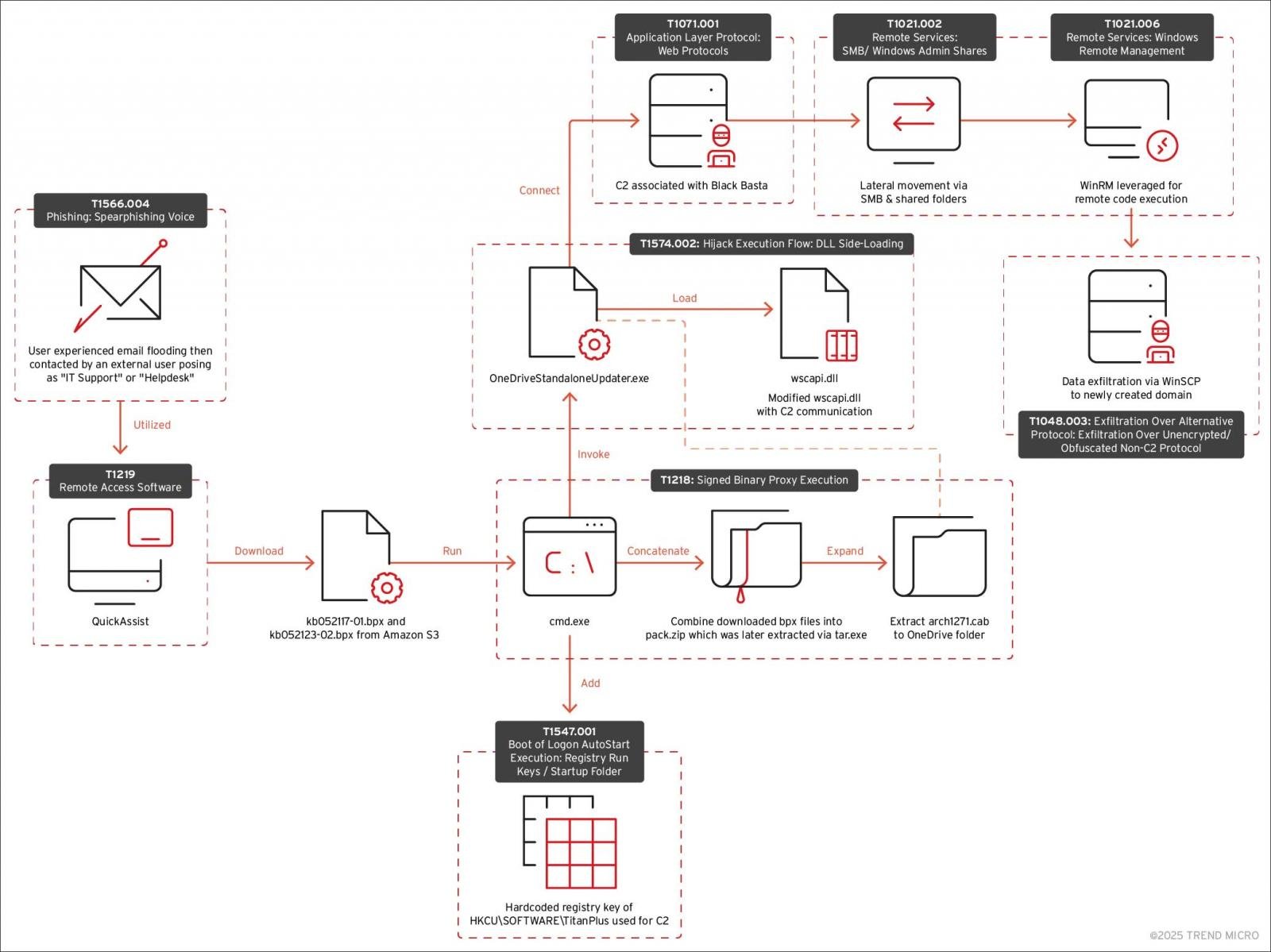
The extortion gang traditionally used Qakbot to procure preliminary get admission to to company networks. Alternatively, after the 2023 legislation enforcement operation violated QBOT operations, the Black Basta operation used to be in search of selection malware for violation of networks.
The gang of the gang to BackConnect means that they’re nonetheless operating with builders attached to the QBOT operation.
Within the new Development Micro document, researchers discovered that the Ransomware Crew crew additionally makes use of Backconnect in assaults, which signifies a possible accident amongst individuals between each teams.
Then the actors of the threats will probably be contacted with the Microsoft command, presenting as an IT reinforce provider as an worker, in the long run deceiving the sufferer in offering far flung get admission to via Home windows Fast Lend a hand.
Whilst the assault flow for black assaults Basta and the cactus isn’t an identical, they have been very equivalent, whilst the micro -the risk that makes use of command and keep watch over servers, normally related to the Black Basta.
 Cactus assault
Cactus assault
Supply: Development Micro
The length of Gransomware seemed at first of 2023 and has since aimed toward quite a few organizations the usage of techniques very similar to black basta.
BleepingComputer earlier reviews at the cactus additionally confirmed the connection between two extortion gangs, and the cactus used the PowerShell script known as Totalexec, which used to be incessantly observed within the assaults of Black Basta Ransomware.
As well as, the Black Basta Ransomware Gang followed the encryption process, which used to be at the beginning distinctive for assaults from the cactus -robbers, which additional bolstered the relationship between each teams.
The overall use of techniques, comments and different operational similarities raises questions on whether or not the cactus is anger, is a rebrey of a black basta or just a accident between the members.
However, BleepingComputer came upon that Black Basta slowly disappears since December 2024, and their position of leakage in self sufficient mode for many of 2025.
It’s believed that lots of the Black Basta individuals have already begun to transport to different mentor gangs, comparable to cactus, and the new knowledge leak used to be the closing nail within the coffin.



