Microsoft got rid of the undisclosed selection of GitHub repositories utilized in a big -scale multicuating marketing campaign, which influenced virtually 1,000,000 units around the globe.
The corporate’s danger analysts came upon those assaults in early December 2024 once they watched the loading of a number of units loading malicious systems from the GITHUB, malicious tool, which was once therefore used to deploy numerous different helpful quite a bit on compromised methods.
Having analyzed the marketing campaign, they discovered that attackers presented promoting within the video on unlawful pirated streaming web sites, which redirect possible sufferers to the malicious Github repositories underneath their regulate.
“Stream web sites introduce imploring redirects to the film for receiving income from a fee for viewing or payment for click from platforms for catches,” Microsoft defined nowadays. “These redirects subsequently sent traffic through one or two additional malicious redirects, ultimately, leading to another web site, such as the Web Sit“ Harming or Technical Support, which is then redirected ”.
Redoverizing movies redirected customers to GITHUB repositors, which inflamed them with malicious tool designed to come across the device, accumulate an in depth device (for instance, reminiscence measurement, graphic main points, solution of the display screen, working device (OS) and consumer tracks) and the exploration of the gathered knowledge when deploying further load quite a bit.
The heavy load of the PowerShell PowerShell script quite a bit Trojan far off get admission to Netsuport Trojan (RAT) from the command and regulate server and establishes fidelity within the rat sign in. After execution, malicious systems too can deploy malicious tool for informing Lumma and an open supply with open supply for Exfiltrate consumer knowledge and browser accounting knowledge.
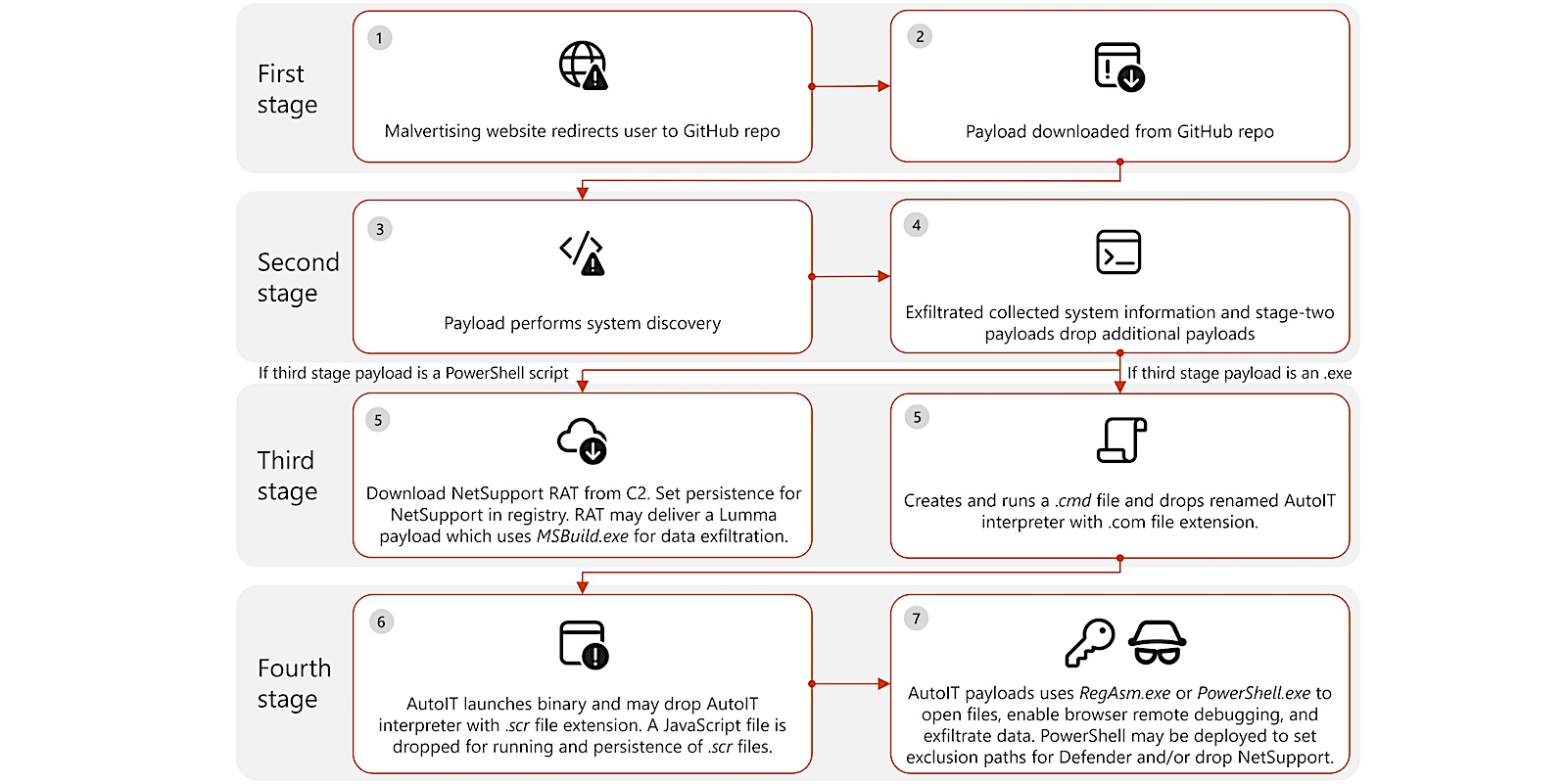 Phases of assault (Microsoft)
Phases of assault (Microsoft)
Then again, if the helpful load of the 3rd level is a executable record, it creates and launches the CMD record, leaving the Autoit renamed interpreter with the .com extension. This Autoit element then launches a binary record and will abandon any other model of the Autoit interpreter with the. SCR extension. The JavaScript record could also be deployed to lend a hand execute and get fidelity for .SCR information.
On the final level of the Autoit, Autoit quite a bit are utilized by Regasm or PowerShell to open information, permit debugging a far off browser and further knowledge. In some circumstances, PowerShell could also be used to arrange exception tactics to protect Home windows or to take away extra helpful plenty of Netsuport.
Whilst GitHub was once the principle platform for putting helpful quite a bit delivered on the first level of the marketing campaign, Microsoft Wreath Intelligence additionally noticed the helpful quite a bit positioned on Dropbox and Discord.
“This lesson is monitored under the umbrella name by Storm-0408, which we use to track numerous actors-thorosis associated with remote access or malicious software, and which use phishing, search optimization (SEO) or default campaign to spread malicious useful loads,” mentioned Microsoft.
“The campaign influenced a wide range of organizations and industries, including both consumer and corporate devices, emphasizing the indistinguishable nature of the attack.”
The Microsoft document comprises further and extra detailed details about quite a lot of phases of assaults and helpful quite a bit used within the multi -stage assault chain of this advanced imploring marketing campaign.



