Prior to now, unregistered malicious device of Polyglot is deployed in assaults in opposition to aviation, satellite tv for pc communications and important shipping organizations within the United Arab Emirates.
The adoption is equipped via a bacdor referred to as Sosano, which units perseverance on inflamed gadgets and lets in attackers to execute instructions remotely.
The lesson used to be found out via Pressispoint in October 2024, which states that the assaults are hooked up with the actor of threats named “Unk_craftyCamel”. Even supposing the marketing campaign continues to be small, researchers document that it’s nonetheless complex and threatening for centered firms.
Researchers Proofpoint famous that assaults are very similar to operations from teams aligned via Iranian, TA451 and TA455. Nonetheless, the closing marketing campaign differs from serious focusing cyberppying.
The specter of polyglot
Undowed with polyglot is composed of specifically created information that comprise a number of report codecs, which permits them to interpret them with more than a few programs.
As an example, one report may also be structured as the true MSI (Home windows installer) and Jar (Java Archive), because of which Home windows acknowledges it as MSI, whilst the Java execution time translates it as Jar.
This technique lets in attackers to imperceptibly ship malware, evading safety device, which in most cases analyzes one structure.
The archive incorporates the LNK report (Home windows label), disguised as XLS, in addition to two PDF information (“AAAA East-dic.pdf” and “Electronica-2024.pdf”). Each PDF information are Polyglot information containing the felony construction of the PDF report, however an extra malicious construction of information.
The primary PDF incorporates the HTA code (HTML -Appendix), and the opposite comprises the hidden ZIP archive.
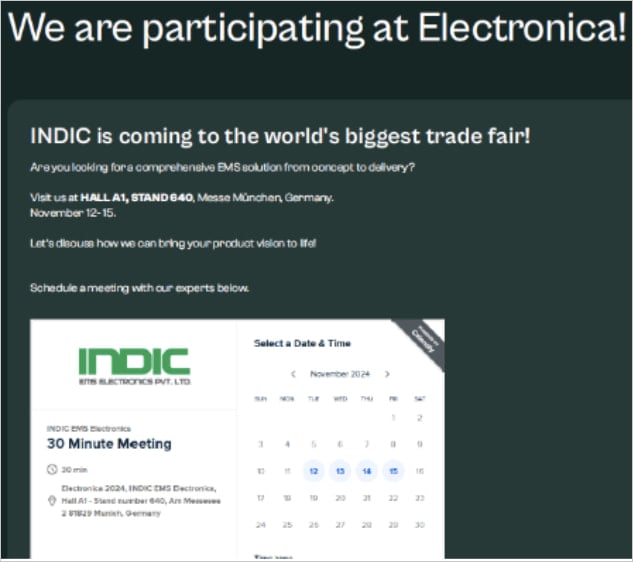 Some of the PDF bait utilized in assaults
Some of the PDF bait utilized in assaults
Supply: Proofpoint
The principle benefit of the use of polyglot is evasion, since maximum safety equipment will check up on the primary report structure (PDF), which is a benign file and fully forget about the malicious hidden phase (helpful lots HTA/ZIP).
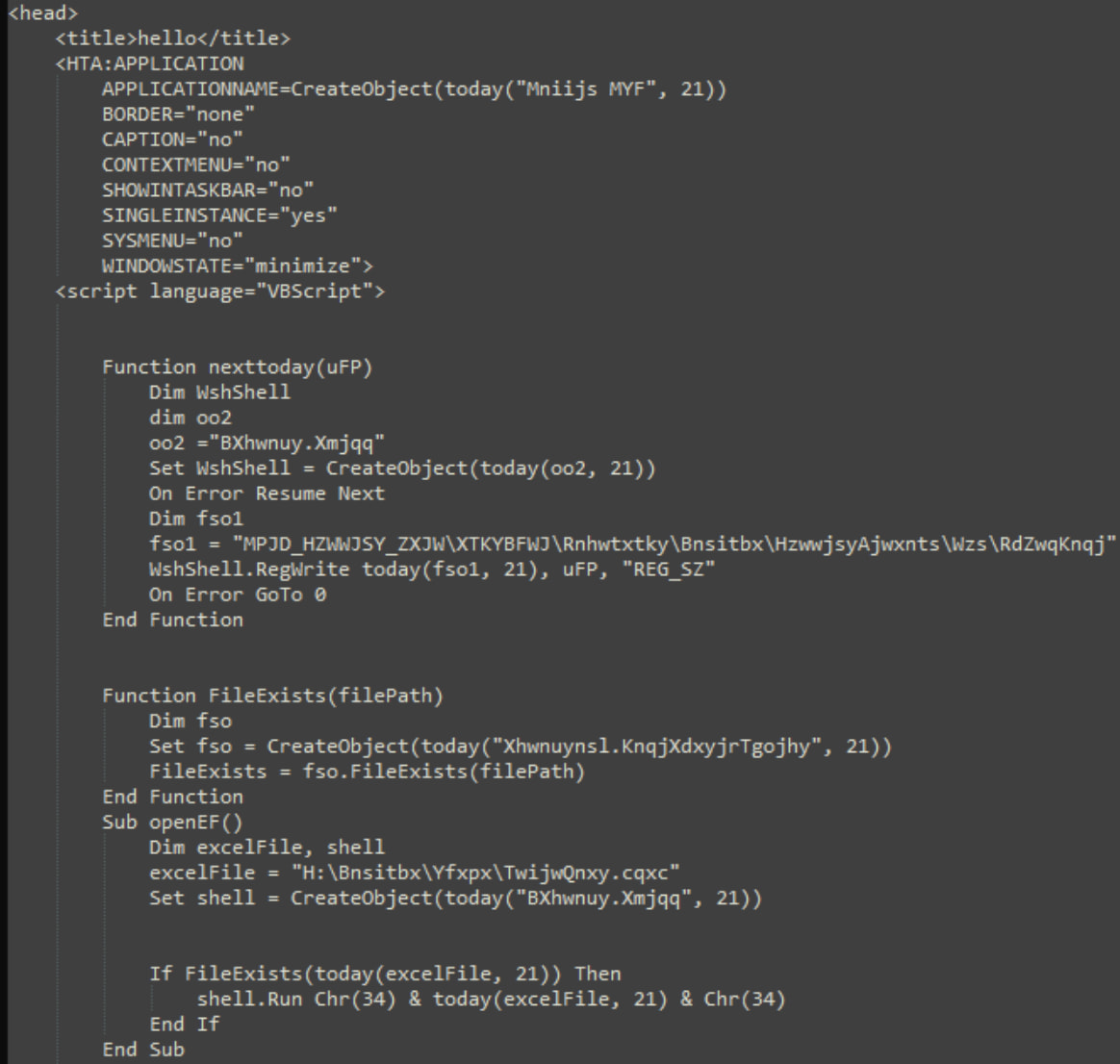 HTA PARTION in PDF report
HTA PARTION in PDF report
Supply: Proofpoint
When executing the LNK CMD.exe report, it launches mshta.exe, which plays the HTA script hidden within the first PDF, beginning the release of the second one PDF report.
The hidden archive within the second one PDF writes a URL report within the Home windows registry for fidelity, after which plays the encoded JPEG Xor Report, which decodes the helpful load DLL (“YouRdlfinal.dll”), which is Sosano Backdoor.
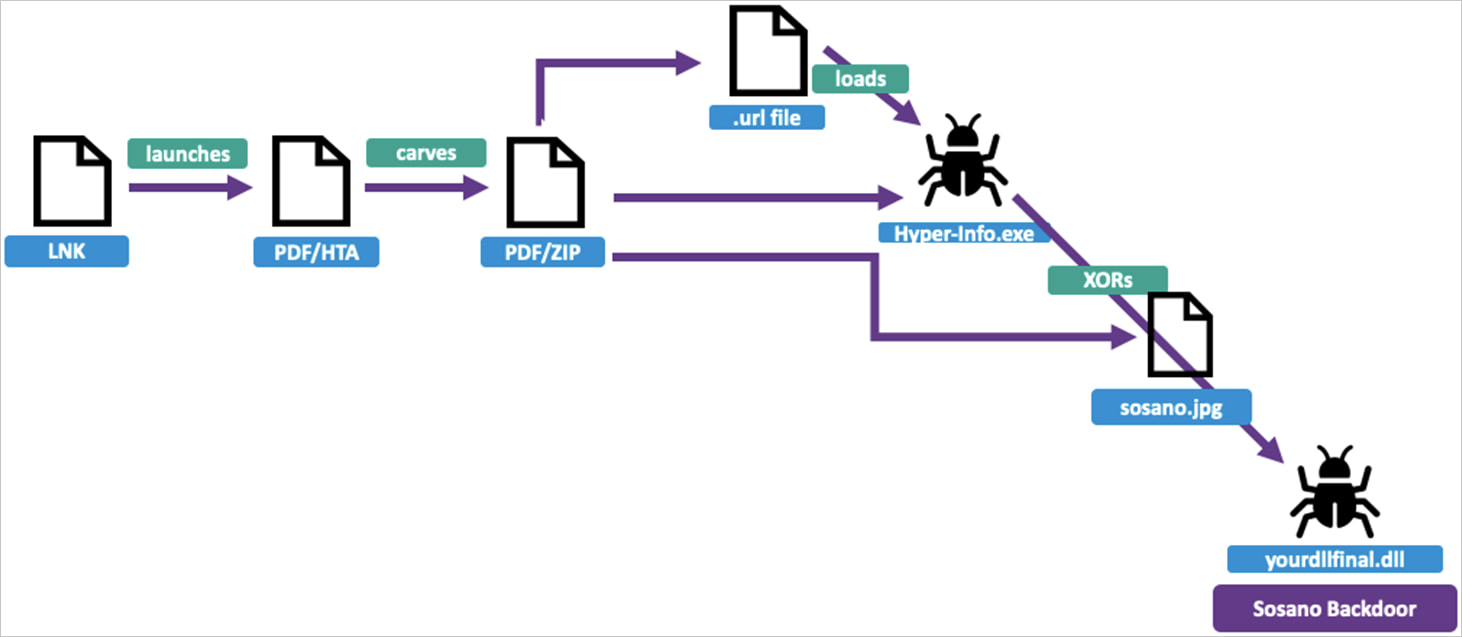 Overview of the an infection chain
Overview of the an infection chain
Supply: Proofpoint
Proofpoint says that Sosano is a slightly easy helpful load in accordance with GO with restricted capability, which used to be most likely inflated to twelve MB to confuse, what small volumes of malicious code it makes use of.
After it’s activated, Sonaso establishes a reference to its command and keep watch over server (C2) on the deal with “Bokhoreshonline (.) COM” and expects instructions, together with report operations, appearing Shell command, in addition to the receipt and release of extra helpful lots.



