The brand new extortion operator with the title “Mora_001” makes use of two Fortinet vulnerabilities to get unauthorized get admission to to the firewall units and the deployment of the custom designed load at the dubbed SuperBlack.
Two vulnerabilities, each authentication bypass, are CVE-2024-55591 and CVE-2025-24472, which Fortinet printed in January and February, respectively.
When Fortinet first printed CVE-2024-55591 on January 14, they showed that it was once operated as a 0 day, and Arctic Wolf mentioned that it was once utilized in assaults since November 2024 to violate Fortigate firewalls.
It’s embarrassing that on February 11, Fortinet added CVE-2015-2447 to their January advisory session, which pressured many to consider that it was once a not too long ago operated flaw. However, Fortinet mentioned to BleepingComputer that this mistake was once additionally fastened in January 2024 and was once no longer operated.
“We do not know that the CVE-2025-24472 is ever operated,” mentioned BleepingComputer Fortinet at the moment.
However, on the finish of January 2025, they discovered that on the finish of January 2025 they came upon that on the finish of January 2025 they came upon that on the finish of January 2025 they came upon Superblack assaults, and the actor of the danger used CVE-2015-24472 on February 2, 2025.
“While Forescout himself did not announce the operation of 24472 for Fortinet, since one of the affected organizations with which we worked shared the results of our investigation with the Psirt Fortinet team,” Forescout BleepingComputer mentioned.
“Soon after this, Fortinet updated his consultant on February 11 to confirm the CVE-2025-24472, as actively operated.”
BleepingComputer contacted Fortinet to explain this second, however we’re nonetheless looking ahead to a solution.
Superblack Ransomware Assaults
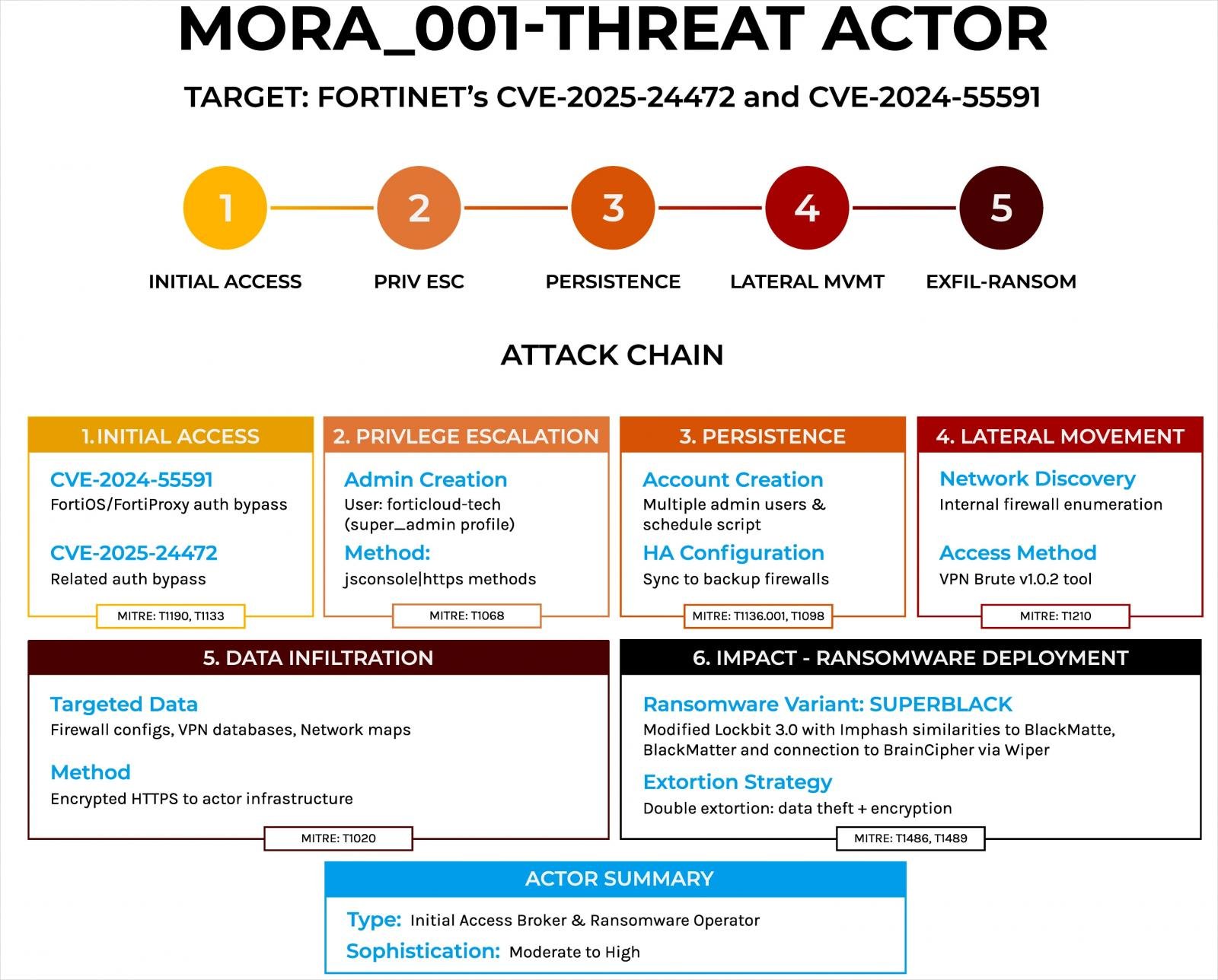
Forescout says that the Mora_001 extortion operator follows a extremely structured assault chain that doesn’t fluctuate a lot in sufferers.
In the beginning, the attacker receives Super_admin ‘privileges the use of two Fortinet deficiencies the use of the JSCONSOLE webSocket assaults or sending direct HTTPs within the detected firewall interfaces.
Additional, they devise new administrator accounts (Forticloud-Tech, Fortigate-FireWall, Adnimistrator) and alter automation duties to recreate them in case of removing.
 Overview of the assault chain Mora_001
Overview of the assault chain Mora_001
Supply: Forescout
After that, the attacker presentations the community and tries the facet motion the use of the stolen VPN accounting knowledge and the newly added VPN accounts, Home windows (WMIC) and SSH keep an eye on equipment and Tacacs+/Radius authentication.
Mora_001 intercepts the information the use of a person software prior to encrypting information for double extortion, figuring out the concern of record servers and database and area controllers.
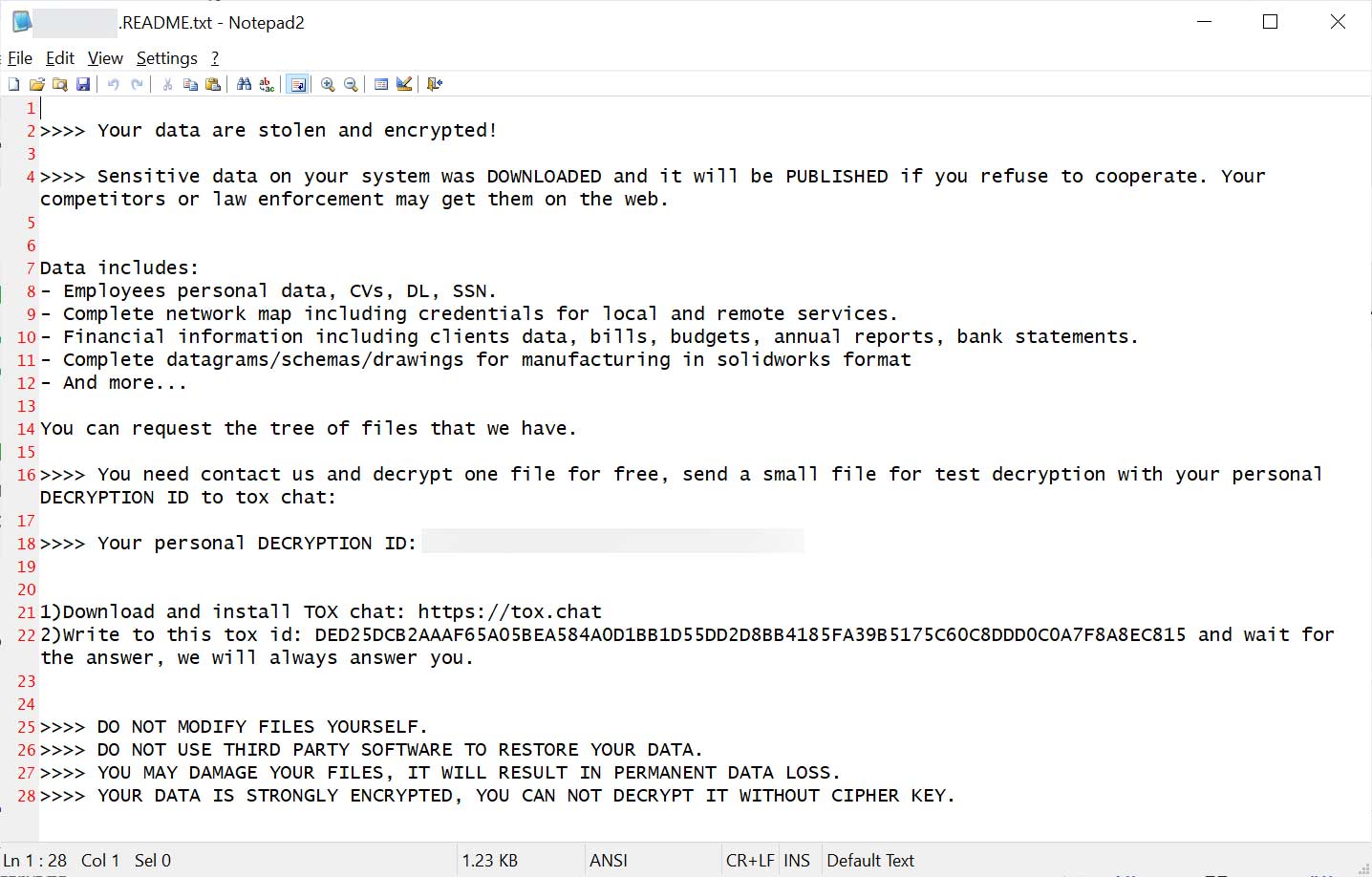
After the method of encryption, the notes of the ransom are dropped into the sufferer device. Then the person wiper is deployed, known as the “WipeBlack” to take away all strains of the executable extortion record to stop forensic research.
 Superblack Ransom Be aware
Superblack Ransom Be aware
Supply: Forescout
Superblack hyperlink to Lockbit
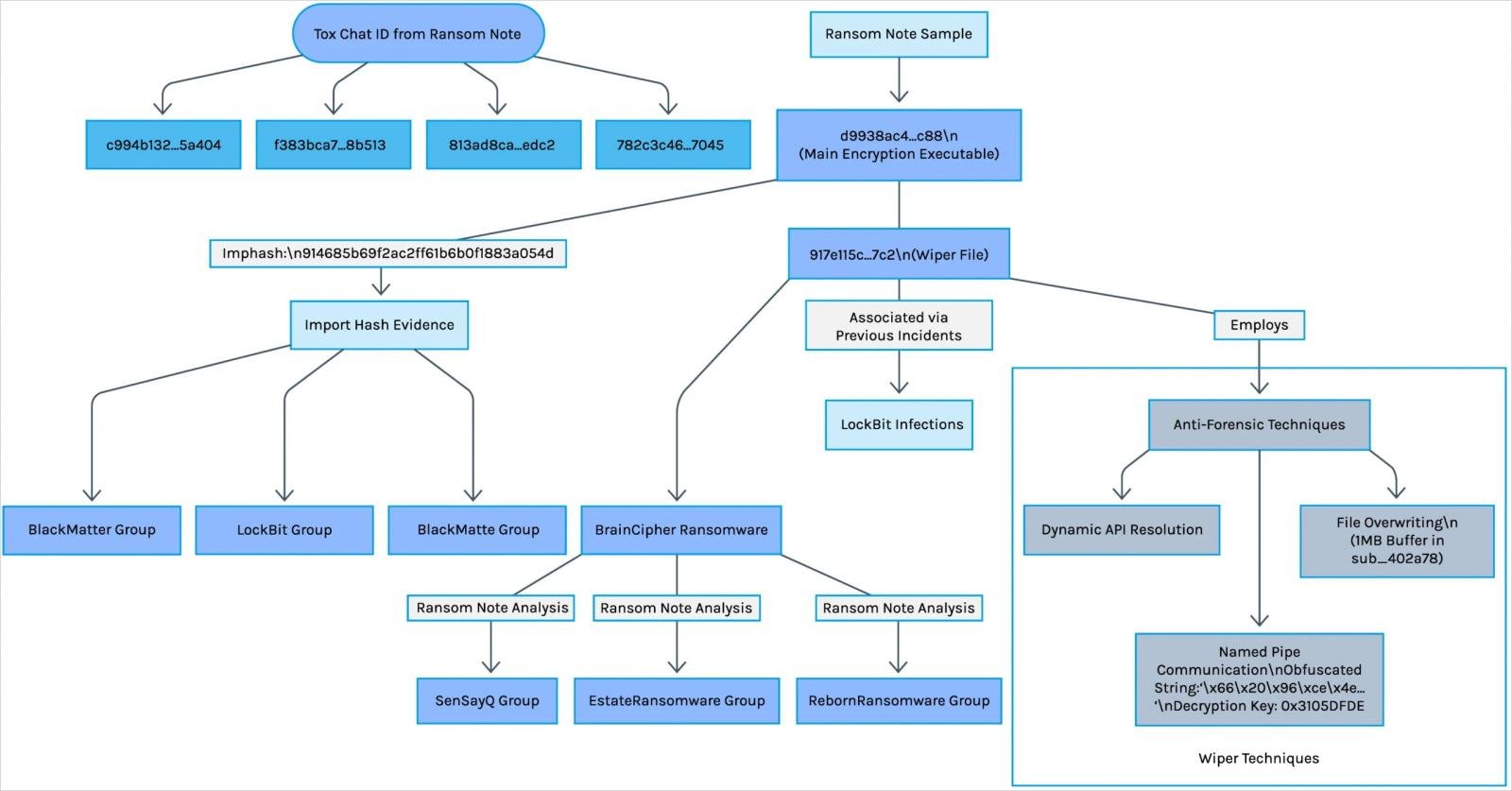
Forescout came upon intensive proof indicating robust ties between the SuperBlack extortion beef up and LockBit extortionist, even though the primary, in keeping with the visual, acts independently.
The primary part is that Superblack Encryptor (Virustotal) is in line with the Lockbit 3.0 leak leak, in which there’s an equivalent construction of the payload and encryption strategies, however the entire authentic branding stripes.
 Courting scheme in line with current proof
Courting scheme in line with current proof
Supply: Forescout
Secondly, Be aware Superblack Ransom Be aware contains the TOX chat identifier related to Lockbit operations, suggesting that Mora_001 is both a former Lockbit spouse or a former member of its major group that manages to pay and negotiations.
The 3rd part, suggesting that the hyperlink is an in depth IP -address blockading with earlier Lockbit operations. As well as, WipeBlack extensively utilized Brancipher Ransomware, Estateransomware and Sensayq Ransomware, all Lockbit hooked up to Lockbit.
Forescout shared an in depth listing of compromise signs (IOC) related to the assaults of Superblack extortion on the backside of his record.

In line with the research of 14 -meter malicious movements, in finding the ten easiest strategies of Miter Att & CK, status for 93% of assaults and the way to offer protection to your self from them.
Learn Purple Document 2025



