The Serbian government had been reported that the Android-Wilm Operation community evolved by way of Cellebrite used to be used to unencumber the instrument of the scholar activist within the nation and check out to put in Adware.
Cellebrite is an Israeli virtual forensic corporate that develops equipment utilized by regulation enforcement businesses, intelligence businesses and personal corporations to extract information from smartphones and different virtual units.
Corporations akin to Cellebrite are generally utilized by 0 day exploits to get admission to and extract information, generally secure on blocked telephones.
Using this Android Exflict used to be discovered within the AMNESTY World Safety Laboratory in mid-2024 throughout forensic clinical research within the journals of the influenced instrument.
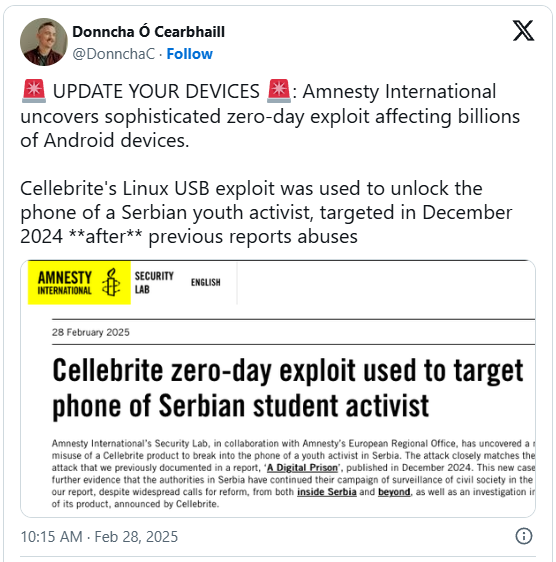
The group in the past reported circumstances of violation of the rights to confidentiality in Serbia in December 2024.
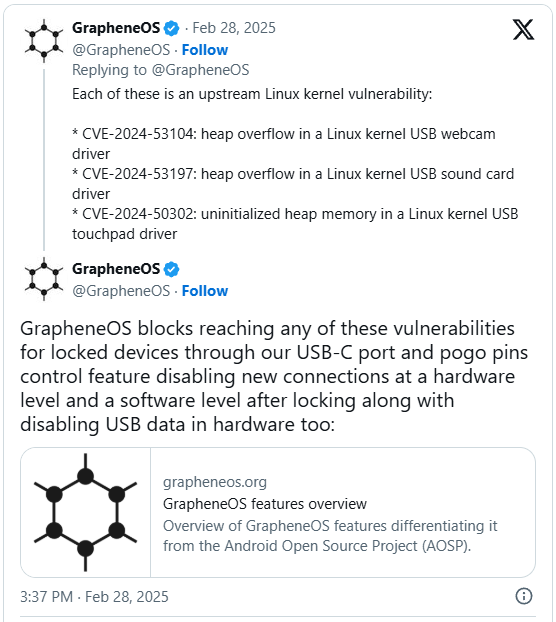
After Amnesty shared her conclusions with the Google (TAG) risk research crew, Google researchers had been in a position to as it should be decide the 3 vulnerabilities in Linux USB USB drivers, additionally utilized in Android, that have been used within the type of 0 days.
3 shortcomings:
- CVE-2024-53104 (USB Video Elegance Exploit)
- CVE-2024-53197 (ALSA USB-SOUND DRIVER Exploit)
- CVE-2024-50302 (USB Concealed Tool Exploit)
The primary problem used to be mounted in Google updates in February 2025 Android Safety, marked as “under limited targeted operation”.
The opposite two deficiencies have no longer but been declared as mounted through which advertisements of the Android Safety replace, and relying at the fashion of the instrument and the way steadily producers replace its core, this may increasingly take a little time.
The top of the protection laboratory in Amnesty, Donncha O’karbhal, stated to BleepingComputer that the CVE-2024-53104 correction could also be sufficient to damage all of the running chain, despite the fact that they can’t but be sure that of this.
GrapheneOS advised BleepingComputer that their distribution of Android already has patches for the CVE-2024-53197 and CVE-20124-50302, as a result of they often replace the newest Linux nucleus.
BleepingComputer requested Google when corrections for 2 shortcomings can be to be had to all Android customers, however we nonetheless be expecting a solution.
USB leaders underneath fireplace
USB -Exflines generally use vulnerabilities within the USB instrument machine akin to drivers, firmware or elements of the nucleus to acquire unauthorized get admission to or regulate over the machine.
Exploit can succeed in reminiscence injury for arbitrary code execution, introduce malicious instructions or bypass the lock monitors.
One of the vital mitigating components is they require bodily get admission to to the objective instrument. On this case, and lots of different equivalent circumstances, this requirement used to be simply fulfilled by way of the police who detained an individual and confiscate their instrument.
In April 2024, Google corrected two shortcomings within the 0 day (CVE-2024-29745 and CVE-2024-29748), operated for unlocking telephones with no PIN code, introducing 0 reminiscence ahead of the USB is grew to become on.
Previous this month, Apple corrected the CENTRIT and grey with 0 day (CVE-2025-24200) used to circumvent a restricted USB mode to extract information from the iPhone.
Android does no longer have a right away identical of a restricted USB Apple restricted mode. Nonetheless, customers can nonetheless melt the risk by way of disabling USB (ADB), surroundings the relationship mode to the “only charging” cable, and turning at the complete encryption of the disk (settings → protection and confidentiality → extra safety and confidentiality → encryption and accounting information → Encrypt Telephone).



